Webinar August 12th : Base, Trace, Replace: How to Lay the Foundation for an SAP Security Model

How do you ensure ongoing control of SAP and the right SAP security model?
It can be hard to build the right SAP security model to ensure ongoing control, compliance, and risk management of your SAP landscape. The number of users accessing SAP, the countless number of T-codes, authorization objects, and wild cards, the scope and sensitivity of the information contained by SAP, along with the many ways to define, grant, track, review, and revoke access can make setting up an SAP security model overwhelming. But security does not need to be complex. So how is it possible to create a simple and effective SAP security model? How does one keep things simple, well structured, and comprehensive?

Andy Hartly,
Senior Product Manager,
Security Weaver
Join Andy Hartley as he talks about how to lay a foundation for your SAP security model so that you can relax during audit time. In this webinar, Andy will share how to use automated SAP tools and transactions so that you can easily maintain proper security documentation and build a sustainable, simple, and effective SAP security model.
Click here for details on how to attend the webinar event, and to view the recording following the live session.
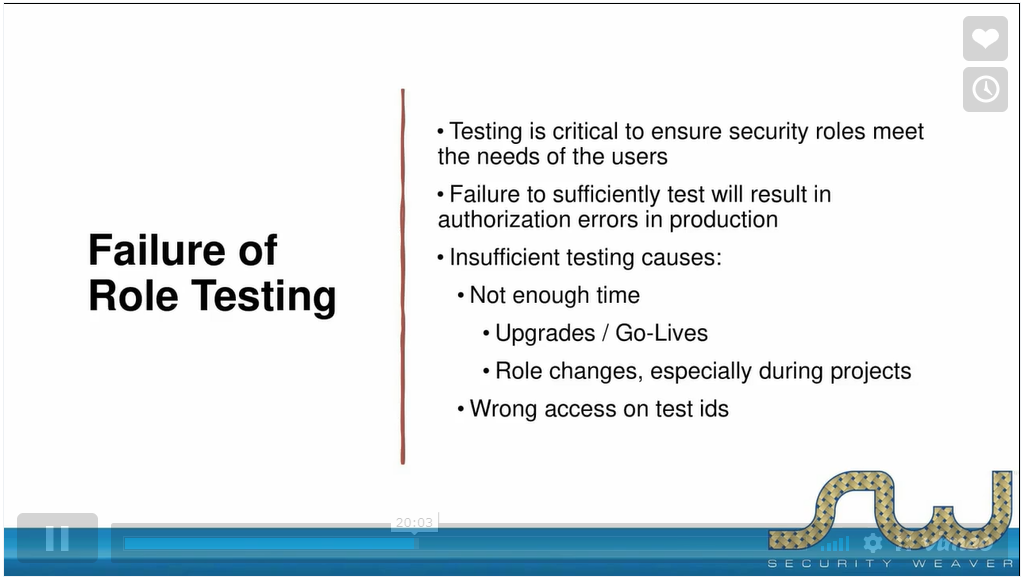
April 15, 2021 - 4 Ways to Handle SAP Security Authorization Errors by Andy Hartley
Avoiding authorization errors and addressing them as they arise can be time-consuming, so streamlining the process can lead to substantial benefits both to administrators (who spend less time troubleshooting and resolving issues) and to end-users (who spend less time-escalating issues and waiting for them to be resolved).
Watch Full Video