January 20th, 2022 - 6 Critical SAP User Actions to Watch For by Issac Kimmel
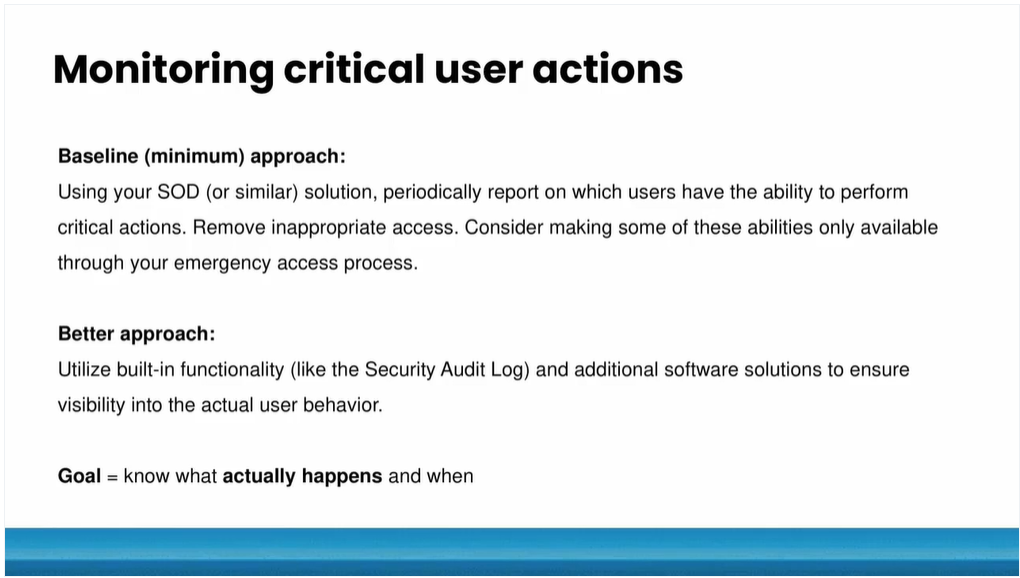
Discuss six specific use cases involving SAP critical user actions, why they are important, and how to solve these problems through automation.
January 13th, 2022 - What is the fastest way to handle your SAP authorization errors? by Miguel Hernández Azpeitia
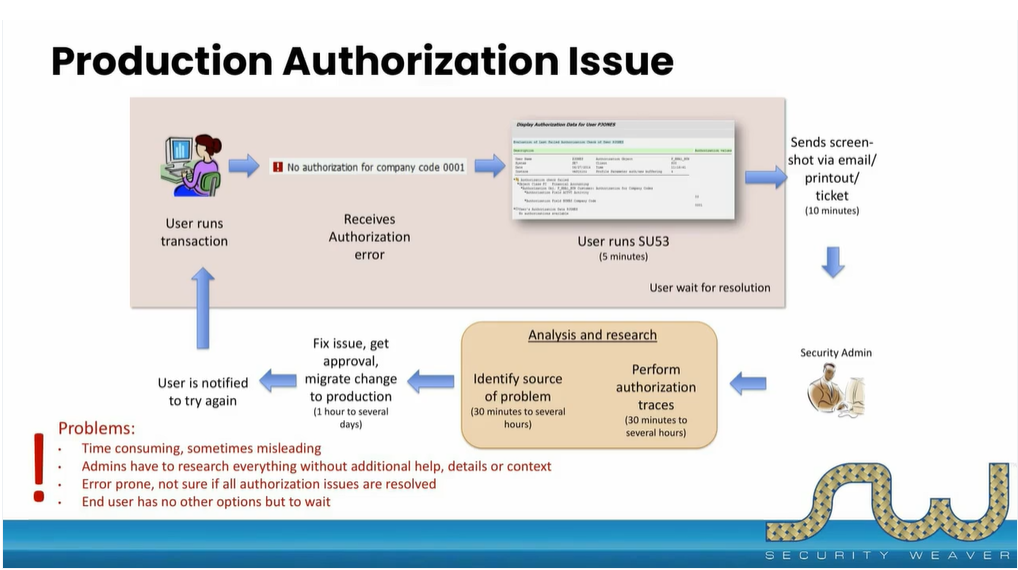
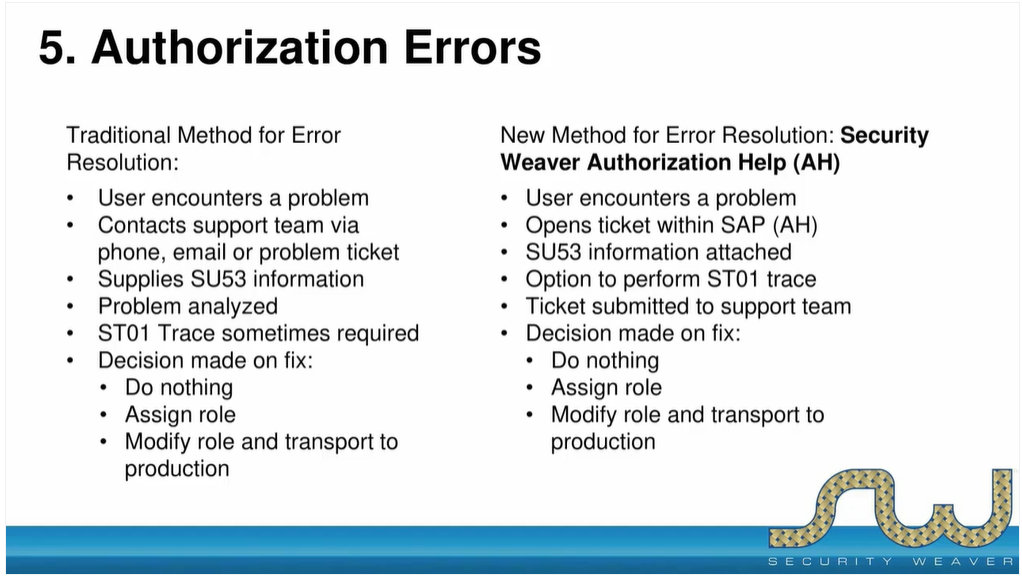
Learn the benefits and shortcomings of SU53 and how automation can resolve authorization errors more quickly, simplify the support process, and keep end-users informed.
December 09th, 2021 - Did You Stop Before SAP Security Became Efficient? by Devin McLaughlin
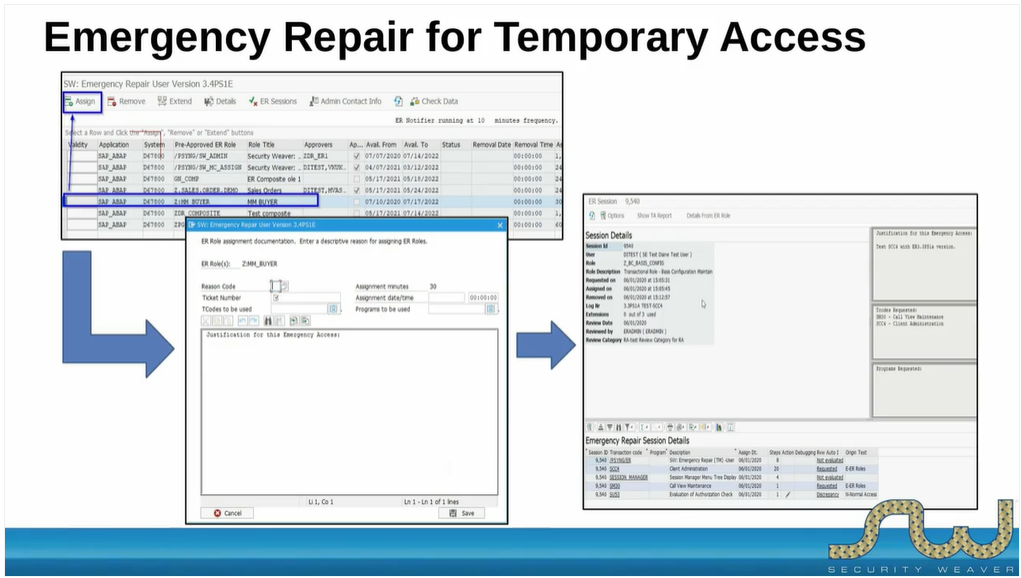
Learn processes and tools that can help you get the most from your security investments and ultimately save you money while simultaneously improving your SAP security.